A Routing Layer on the Internet that garuantees Net-Neutrality
A truly net-neutral Internet would not censor, shape or manipulate traffic selectively. A versatile large-scale routing layer that enforces net-neutrality would make this feasible, enabling global unrestricted Internet access, especially for those in repressive regimes who need it the most. An onion-encrypted routing network provides part of the solution, but the main benefits are lost if access to the network is easily censored, and when participation disincentives prevent adoption.
We propose a solution to censored network access using encapsulated traffic indistinguishable from ordinary traffic, while employing several anti-censorship strategies resting on collateral freedom. Additionally, defining appropriate roles that compartmentalize potential abuse and legal liability issues improves the likelihood of network participation. Finally, to achieve widespread adoption, scalability, and long term sustainability of the routing layer, we propose a free and open competitive marketplace that encourages strong network effects, provides consumer freedoms, and sensible economic incentives in the form of compensation to participants for services provided.
Introduction
Net-neutrality, anti-censorship and privacy on the Internet has come to rely almost exclusively on centralized trusted third parties such as consumer VPN providers and distributed systems such as Tor. While these solutions work well enough for most users, they still suffer from the inherent risks of various trust-based models, identifiable traits resulting in ease of filtering and blocking, as well as varying limitations and disadvantages that hinder adoption, sustainability, and effectiveness.
Based on a study conducted in 2016, 67% of the connected population was using a censored Internet. More recently net-neutrality protections were repealed in the US, many governments outlaw or control use of personal VPNs, and systems are actively blocked due to their use of end-to-end encryption.
Access to information and knowledge is a basic right, as too is privacy. Organizations, institutions, ISP’s and governments use technical means to prevent access to certain information, to shape and manipulate traffic, and to invade the privacy of users under their control.
In this paper we propose a decentralized sustainable solution for a routing layer on the Internet that enforces net-neutrality based on collateral freedom, compartmentalized liability, increased privacy, and a sound economic model properly incentivizing network participation.
Censorship techniques
Internet censorship consists of three processes 11: prescription, identification, and interference. Prescription determines the what, identification the how, and interference is the act itself of blocking or impairing communication. Identification methods used by censors to classify which traffic should undergo interference can loosely be grouped by address and by content.
By address. Regardless of traffic content, a censor may block or impair communication with certain addresses, such as specific or ranges of IP addresses; and specific or pattern matched domain names. A common counter strategy is to not broadly publicize certain addresses, such as in the case of Tor’s secret bridge relay nodes.
By content. A censor may block or impair communication of entire protocols, or specific traffic if certain fingerprints are identified as defined by prescription. An effective identification approach commonly referred to as deep packet inspection (DPI), is the examination of payload data as well as analysis of flow behaviour, packet sizes, and timing. The two common counter strategies to this are by crafting traffic to appear unlike prescription defined traffic, and to camouflage communication to resemble allowed traffic.
In addition, a censor may utilize real-time heuristic assessment, machine learning and active probing to improve their prescription and identification processes. For example, an active probing censor would scan addresses either proactively or on-demand when an address or traffic is suspect, and trigger an update to its address and or content prescription upon successful identification.
We need a way to circumvent these processes and techniques, while reducing the technological arms race. To accomplish this, we need not only address the identification process, but the prescription process as well - by appealing to the censors self-interests. The censor needs to choose not to block addresses or suspected circumvention traffic, as failing to do so would harm its interests due to lost economic and or social value.
Collateral freedom
The solution we propose begins with collateral freedom, an anti-censorship strategy which stems from the term collateral damage, meaning the inadvertent or accidental damage, or loss of value caused by censoring a resource. This is especially harmful to the censor if the blocked resource or content has economic, political, and or social value.
The collateral freedom approach is only possible when three properties exist: the censor chooses to allow traffic to and from a resource; the resource supports handling circumvention traffic; and, the circumvention traffic is indistinguishable from ordinary traffic.
To successfully implement this strategy, we will need to use a technique similar in concept to that of domain fronting, but rather than relying on Server Name Indication (SNI), the Host Header, and existing fronting capable web-services, we propose the use of specifically developed software deployed on cooperating TLS terminating relays providing the functionality required.
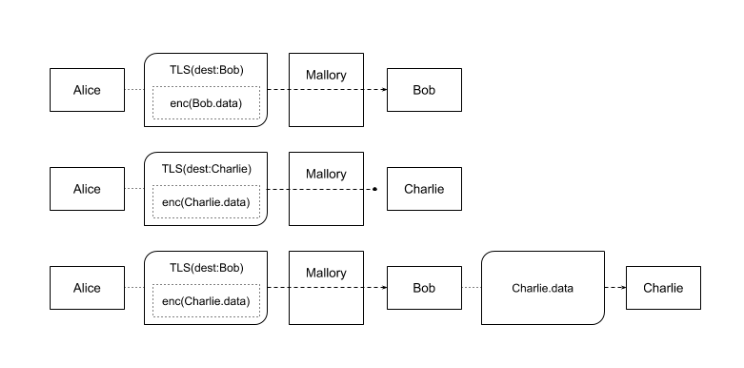
TLS encapsulated traffic and TLS terminating relay. Web services and their use of HTTPS are prolific on the internet, so it is logical to use TLS as the encryption layer. Additionally, the specifically developed software should facilitate encapsulated protocol agnostic payloads, supporting a large range of use-cases.
A TLS terminating relay could be a regular web server (e.g., Apache, Nginx), a load balancer (e.g., HAproxy, Nginx), or an SSL termination type service (e.g., Cloudflare, Akamai, Netlify). In the web server example, it would accept traffic as usual and perform its regular operations, as well as a side job of handling circumvention traffic via a drop-in web server module. Once the web server has negotiated the TLS handshake of a session and the first layer of encryption stripped, the module would be able to identify a session payload as circumvention traffic and handle it.
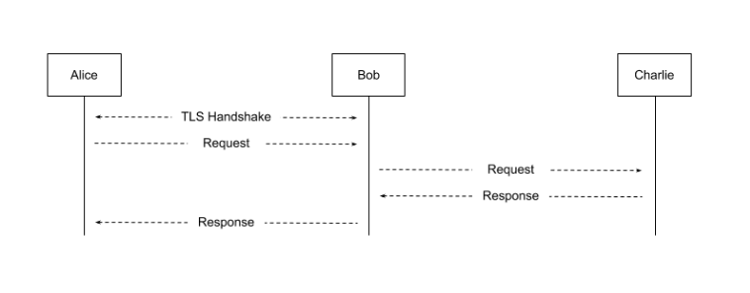
Fronting bridge relay. We define a cooperating TLS terminating relay capable of handling circumvention traffic as a fronting bridge relay, in part due to the concept similarities with domain fronting, providing a bridge to the routing layer and acting as a traffic relay. In addition to high-value resources which have economic and or social value, complementary strategies could be employed, such as overwhelming the censors filtering capabilities. This could be achieved with wide-scale adoption, as well as strategically selected IP addresses adjacent to a high-value resource (IP range of +/- 1) removing the ability of utilizing IP range blocking rules and instead requiring dedicated rules per fronting bridge relay.
In this single-hop scenario, several potential problems become apparent for both the user as well as relay providers. As with consumer VPNs, this scenario introduces trust and privacy issues for users, although they could be addressed in part by chaining multiple fronting bridge relays together. For relay providers, the potential problem of legal liability could pose a major barrier to participation.
Compartmentalized liability
A relay provider allowing arbitrary connections to the Internet, such as a Tor exit node, comes with a risk profile many participants may shy away from due to the potential abuse and legal liability 23, inhibiting adoption. A whitelist strategy might provide some relief, but this does not solve the issue and, counter-intuitively introduces a type of censorship. Instead, we propose compartmentalizing this liability to a specific role fulfilled by organizations already equipped to handle these liabilities.
Backing bridge relay. Named for their position of importance on the network, the highest liability role, and abuse handling willingness to accept exposure to potential legal pressures, raids, seizures, warrants, NSLs, lawsuits, IP blocking, DMCAs and political profiling.
Any entity may provide backing bridge relay services, however as providers in the consumer VPN space are already equipped to handle these liabilities, they are most likely to fill this role. Backing bridge relays, running a subset of the specifically developed software, would accept connections from fronting bridge relays, terminate the internal session, and relay the traffic to the destination.
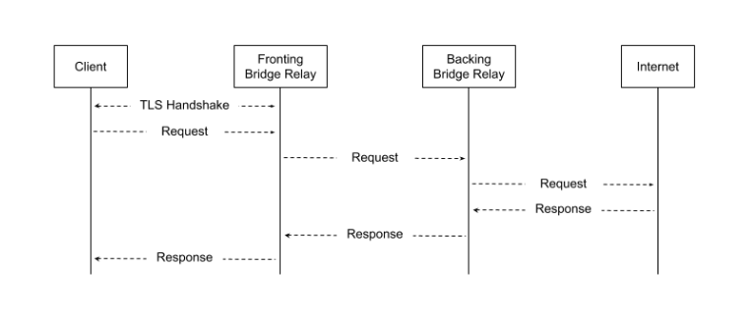
By including backing bridge relays in the network circuit, it removes the potential abuse and legal liability issues from fronting bridge relays, increasing the likelihood for participation. Additionally, user identity privacy is potentially increased due to the added relay.
Increasing privacy
The traditional digital privacy model achieves a level of privacy by limiting information disclosure to the parties involved. In the context of a user, we broadly define privacy by two aspects: identity and activity. By employing targeted encryption in tandem with increasing the degrees of separation between parties involved, a higher level of privacy could be achieved.
Onion encryption and routing. In an onion network, messages are encapsulated in layers of encryption, analogous to layers of an onion. The encrypted data is transmitted through a series of network nodes called onion routers, each of which “peels” away a single layer, revealing only the information required by the node to perform its job. Required information could include the data’s next destination address, resulting in each intermediary knowing only addresses of the immediately preceding origin and the immediately following destination.
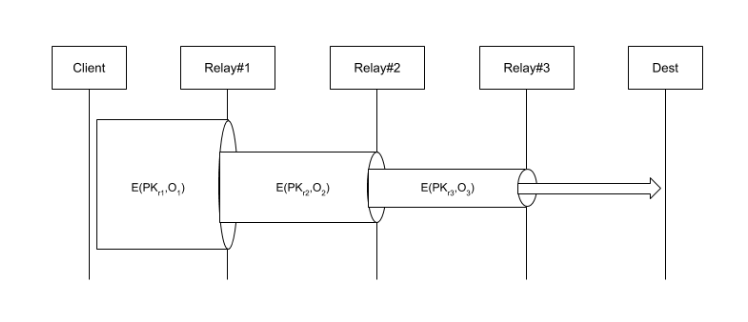
Although multiple fronting and or backing bridge relays could be chained together to create a network circuit, we propose a third relay type.
Entropic relay. Named for its role in increasing entropy, would accept traffic from either a fronting bridge relay or another entropic relay, and relay the traffic to another entropic relay or a backing bridge relay, by which increasing the degrees of separation between parties involved. Similar to Tor’s middle relays, entropic relays have the least direct exposure to potential liability issues, as such we suspect this will lower the bar for participation resulting in greater adoption and scaling, leading to strengthened privacy, anonymity and plausible deniability for the entire network.
In the case where a fronting bridge relay is not needed to circumvent censorship, an entropic relay could potentially accept traffic directly from a client. In addition, an alternative network protocol could be employed between the client and an entropic relay to increase performance.
Scalability and sustainability
A major pitfall of any distributed system is its widespread adoption, hindering on which is the scalability and long term sustainability of the system. To address this, we propose a free and open competitive marketplace of service contracts, encouraging strong network effects, providing consumer freedoms, and sensible economic incentives, while facilitating compensation for services provided.
Service contract. Service contracts may be created by any party, and compete for both consumers and service providers. They are flexible in both their logic and defined parameters (e.g., price, duration, bandwidth, etc.). Once created, service providers may enroll, and be compensated based on their proof of service provided. Service contracts are pre-paid, further improving the user experience as well as guaranteeing service provider compensation via escrowed funds. Service contracts are enacted when funds are received, generating a service key.
Service key. Service keys are valid based on the service contract parameters, and are temporary. By design, they increase the degrees of separation between payment information and network usage, resulting in improved user privacy as well as transferability and resalability. Resalability also enables the purchase of service keys with any payment method accepted by the seller, further improving the user experience and consumer freedom. The purpose of a service key is to generate share tokens.
Share token. Share tokens serve a dual role. First by allowing a way for service providers to authorize service. And second, as a representation of value if proven valid for the service provided. Share tokens are cryptographically and independently generated by a client specifically for each service provider in the routing path, and included in the appropriate encrypted onion layer of traffic being sent. The frequency of which is based on the service contract. Service providers accumulate share tokens to later submit for validation and compensation.
By employing a proportional share-based model [R = (Kv * n/N) - Cf] similar to that used in cryptocurrency mining pools, compensation or reward (R) is split between service providers according to the number of valid share tokens (n) they accumulate in proportion to the total number of valid share tokens (N) submitted by all service providers for a specific service key (Kv) backed value, less the service contract payout fee (Cf). In other words, all shares are equal but their value is calculated when the settlement window closes as defined by the service contract and service key expiration.
Conclusion
We have proposed a sustainable solution for enforcing net-neutrality on the Internet by means of a dedicated routing layer.
We started with an anti-censorship strategy appealing to the censors self-interests based on collateral freedom, circumventing the censor and providing entry to the routing layer via fronting bridge relays, but alone is incomplete due to potential privacy, trust and legal liability issues.
To solve these, we proposed employing targeted encryption in tandem with increasing the degrees of separation between parties involved, as well as compartmentalizing potential abuse and legal liability issues to the backing bridge relay role fulfilled by organizations already equipped for handling said issues.
We finished off with a proposal addressing scalability and sustainability of the routing layer by means of a free and open competitive marketplace of service contracts, encouraging strong network effects, increasing user privacy, and providing consumer freedoms and sensible economic incentives to service providers, while facilitating compensation for services provided.
